Risks and Mitigation of Insider Threats

Insider attacks are growing, whereby 60% of organizations in the past year alone have suffered employee-related data breaches. Surprised? Most businesses get blindsided by the people they put their most trust in. It can be accidental data leaks or malicious actions, but the risk is very real and, regrettably, on the rise. It’s no longer a matter of “if,” but rather “when” an insider threat could compromise your organization’s most sensitive data. So, how do you then protect your business from within?
In this blog, we will talk about the real risks of insider threats and steps taken for preventing them before they spiral out of control. It’s high time to act!
What is an Insider Threats?
Internal threats originate within an organization, whether from employees, contractors, or partners with sensitive information or systems. These lead to data breaches, financial loss, or reputational damage in the case of abusive access, be it intentionally or through negligence. The thing with insider threats is that they are hard to detect because these are coming from people you would not suspect. That same trust is a way to bypass any default security measures.
This challenge can only be met by those who respond quickly and carefully to the individuals who can wreak havoc among us.

Insider Threats in Cyber Security
Insider threats are one of the biggest challenges in cybersecurity today. Why? Because insiders have access to critical systems and data, making it hard to spot the difference between routine actions and potential risks. As Kevin Mitnick said, “The human element is the weakest link in security.”
So, how do you protect your business from within without disrupting everyday operations? It’s all about having a smart insider threat program that keeps your systems safe while staying efficient.
Types of Insider Threats
Here’s a quick breakdown of insider threat types for easy understanding:
- Malicious Insiders: These people deliberately harm the company. They might do it for personal gain, revenge, or because someone from outside convinced them. Their actions are intentional and dangerous.
- Negligent Insiders: These are not bad people, but their mistakes can be costly. They might mishandle data, forget security rules, or fall for scams like phishing. Their lack of care can lead to serious problems.
- Compromised Insiders: These insiders don’t know they are a threat. Outside attackers trick them through things like social engineering or malware, turning them into unknowing accomplices.
- Each type needs a different approach to prevent damage. Understanding these types can help you tailor your security approach, including backup encryptions.
Motivational Misuse: A Threat Every CISO Must Address
The insider threat, in most discussions, is always subtle and underplayed—even when it involves motivational misuse. On one hand, workers with access to sensitive data may misuse such data for personal reasons—that is, satisfying curiosity or frustration and, often, even hidden grievances. It doesn’t have to be a financial reward; perhaps an emotional or psychological reason.
For a CISO, it is very important to understand the underlying reasons. Why? This is because most security controls fail to include the human element in their fold. A purely technical approach can leave several loopholes in your defense grid. This calls for a psychological shift. Building resilience into security posture calls for addressing the personal and emotional elements that lead to such behavior.
A proactive approach is to instill an open and ethical workplace culture that talks frequently with employees about ethical behavior and practices of handling data. Present clear guidelines and listen to frustrations or concerns. By nurturing a culture of transparency, you’re less likely to face misuse driven by personal motives.
Understanding that insider threats are as much psychological as technical. This will shape security policies and will better protect your organization.
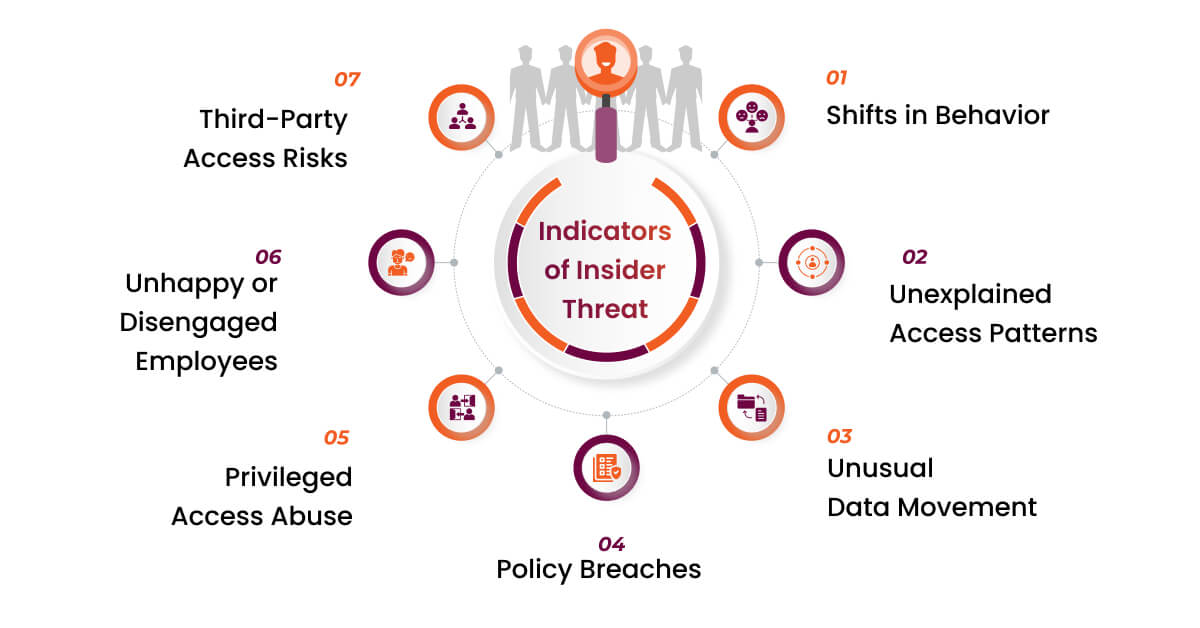
Indicators of Insider Threat
Identifying insider threats is complex, but certain red flags can help you stay ahead of potential risks. Beyond just monitoring technology, it’s about understanding behavior patterns and fostering a secure work culture.

- Shifts in Behavior: An employee who becomes secretive, disengaged, or suddenly stressed might not just be facing personal issues. Combine this with financial trouble, and the risk of malicious intent increases significantly.
- Unexplained Access Patterns: Unscheduled system access, especially outside of normal working hours or from unusual locations, should be a cause for concern. These anomalies often indicate unauthorized attempts to probe sensitive data.
- Unusual Data Movement: Keep an eye on sudden increases in file downloads, large data transfers, or accessing files that don’t match someone’s job duties. These could be early signs of a potential data breach.
- Policy Breaches: Employees who frequently bypass cybersecurity protocols are waving a red flag. While some violations might seem minor, they could signal larger, malicious activities.
- Privileged Access Abuse: Keep an eye on employees with special access to sensitive systems. If they start acting suspiciously, it’s a serious red flag. When someone with higher-level access misuses their privileges, the risk is much greater because they can do more damage.
- Unhappy or Disengaged Employees: Disgruntled or disconnected employees are more likely to cause harm, sometimes out of frustration or for personal gain. Regular check-ins and showing genuine care for their well-being can go a long way in preventing issues from escalating.
- Third-Party Access Risks: Insider threats aren’t just about employees. Contractors and third-party vendors with access to your systems can also be a risk. If their access isn’t monitored properly, they could accidentally or intentionally cause harm.
It is not just about identifying these behaviors but creating such an environment around the workplace where unusual activities can be noticed and investigated in no time. It needs a mix of behavior tracking with employee education and a culture of trust and awareness. Routine audits, smarter monitoring tools, and a security-first approach are the sole ways to catch insider threats before they become bigger issues.
The Impact on Data Protection
When employees or trusted individuals misuse their access, the consequences can be severe. Data can be leaked, altered, or erased, leaving a company vulnerable. And when that happens, it isn’t just the data that’s at risk—legal issues and stakeholder trust hang in the balance.
- Financial and reputational damage
It’s easy to focus on the technical damage insider threats cause, but what about the financial and reputational fallout? The cost of recovering from an insider breach goes beyond data recovery. It includes potential regulatory fines, lawsuits, and lost business opportunities. And let’s not forget the hardest part to fix—reputation. Once customers lose trust, it’s an uphill battle to regain their confidence.
- Operational Downtime:
There are instances where systems need to be inspected, and this contributes to downtime. Productivity is lost, as are operations, which are normally accomplished within a certain timeline. The more the Consternation, the more the Carry over effect to the continuity of business operations.
- Loss of Intellectual Property:
Stolen or leaked data can be caused by an insider in an organization. Such include trade secrets, blueprints and research work. Failure to retain this information may leave you vulnerable to competition.
- Compliance Violations:
Certain regulations like GDPR or HIPAA could be violated in some breaches. This is very common, and it results in heavy penalties and fines. In some cases, lawsuits or penalties may follow.
- Damaged Employee Trust:
Finding an ‘insider’ can lead to trust issues in the workplace. Employees may be apprehensive, which may lower their spirits. It is detrimental to work morale.
- Compromised Data Integrity:
Data may be tampered with, lost, or again used inappropriately by people associated with the company. This compromises the credibility of decisions made from such data. Quite a challenge will be retrieving the accuracy of data.
- Customer Loss:
Clients will tend to lose hope trusting the organization addressing their needs when their security has been compromised. As such, customer churn will be inevitable. It is time and money consuming to regain that confidence.
- Ongoing Recovery Costs:
Redressing the factors that expose staff to insider threats is more than just technological solutions. Monitoring over time, policy reengineering, and training of employees are often requisite. These efforts can be expensive.
Challenges in Detection
Detecting insider threats is tricky because insiders already have access to the organization’s systems, making their actions seem normal. Here’s why it’s a challenge:
- Like Normal Behavior: Insiders’ activities often look like regular work, making it hard to spot when something is wrong.
- System Knowledge: They understand the organization’s systems well, allowing them to hide their actions more easily.
- Late Detection: These insider threats usually remain undetected for a long duration and cause more damage.
- Privacy Concerns: Monitoring employees while respecting their privacy can be tough to balance.
Intelligent tools, like AI and behavioral tracking, may support the early detection of these unusual activities.
Strategies for Mitigating Insider Threats
Insider threats hide in plain sight. So, how does one stay ahead of them? Well, here are a few simple yet powerful steps you might want to consider:
- Raise Employee Awareness: Your employees are your first line of defense. Regular training in cybersecurity helps them recognize suspicious activity and risky behaviors. Make employees a part of the solution, not the problem.
- Limit Access to Data: Not everyone needs access to everything. By giving your employees just what they need for their roles, you minimize the chances of unauthorized access. It is one of those simple moves that makes a big difference.
- Monitor User Activity: Keeping an eye on unusual behavior. These can be someone accessing data they don't usually touch, etc. This can alert you to potential threats early on. Take this measure as a preventive and proactive step.
- Regularly Audit Systems: Every now and then, review who has access to what. Audits aren't just about catching mistakes but about tightening security and making sure nothing slips through the cracks.
- Nurture Open Communication: The less alone an employee is forced to feel, the less probable it is that he will turn disgruntled and act out. A healthy work environment can be your strongest defense against insider threats.
- Establish an Insider Risk Program: The program would help mitigate these threats by developing policies and procedures for the identification, prevention, and response related to insider threats.
- User Activity Monitoring: The system needs to monitor unusual behavior, such as an access event where someone is accessing data that they normally don't touch. And you can look at this form of monitoring as proactive, not paranoid.
- Implement Data Loss Prevention Solution: These solutions are crucial in managing insider threats. They monitor and control data transfers both internally and externally to the organizational network. DLP tools can observe data access or exfiltration by unauthorized users or entities.
- These steps will help you build a culture of security being everyone's responsibility.
Benefits of Implementing Insider Threat Mitigation
Insider threats are often an ignored risk. However, they are some of the most destructive. A good insider threat mitigation strategy is not optional; it’s a must-have. Let’s break down how this can help your business.
- Heads Off Costly Data Breaches
A Cyber Insider Threat Mitigation Strategy Develop an organizational approach that enables the detection and neutralization of such risks before they can become destructive. This proactive approach prevents unauthorized access and data theft and may help engender trust in your customers and partners. In business, trust means everything.
- Ensures compliance with regulations
Compliance with regulations such as GDPR, HIPAA, or CCPA is something with which your organization absolutely must comply. Insider threat management secures data and helps assure the legality of your business.
- Smooth Business Operations
Insider threat mitigation ensures your business operations run smoothly. The protection of critical data saves organizations from downtime and makes them operationally effective to keep the attitude forward-looking.
- Saves You Money
Halting insider-mitigated data breaches saves businesses from major recovery costs, legal fees, and reputation management to invest in innovation and strategic growth.
- Fosters a Security-First Culture
A strong insider threat program gives staff an awareness that sensitive data must be used responsibly. It’s a security-first culture wherein everybody contributes to protecting the organization from internal risks.
How Parablu Keeps Your Data Secure from Insider Threats?
Insider threats are often underestimated but may cause irreparable damage to businesses. Parablu understands that internal risks can be mitigated only by being proactive with your data protection rather than merely deploying technology. Our Zero Trust approach allows access to authorized users alone for certain data, thus limiting inside exposure. Continuous monitoring and auditing in detail allow you to spot suspicious activities well before they turn out to be a danger. Additionally, internal employees cannot misuse sensitive information because of end-to-end encryption.
Parablu provides policy-based controls that give you control over who can access which data, and it is through this that you keep your business ahead of insider threats.
Conclusion
Insider threats pose a significant risk to the security and integrity of organizational data. Implementing a robust insider threat management strategy is essential in data security. Effective insider threat mitigation techniques include:
- Microsoft 365 data loss prevention solutions, which help in detecting anomalous data movement.
- Utilization of data masking and encryption to protect information in transit and at rest.
- Adoption of multi-factor authentication (MFA) to enhance access control.
- Implementing comprehensive managed detection and response (MDR) services to efficiently identify and respond to threats.
By integrating these strategies, organizations can enhance their cybersecurity posture. They can easily mitigate the associated risks with insider threats.






