Privacy vs Security – Why Data Privacy Matters for Businesses

Difference between security and privacy
Privacy vs Security. It is easy to get the two terms confused – and in most conversations, we end up talking about them as if they were the same thing. Privacy and Security may have some things in common but are actually quite different concepts. Security can best be thought of as a form of defense. Privacy is more about control and the freedom to make decisions about what you want to reveal.
One common argument that a lot of privacy advocates encounter is that privacy matters only to people who are secretive or have something to hide. In fact, Google’s then CEO Eric Schmidt infamously once said “if you have something that you don’t want anybody to know, then you shouldn’t be doing it in the first place”.
But this is a flawed argument because it confuses privacy with secrecy. The basic need for privacy isn’t born out of a need to keep a secret, so much as the need to control what information we desire to share and with whom. For example, when we go into a bathroom, we close the door for privacy – not for secrecy.
Read: Data Security and Privacy: What is the Difference?
Why does Privacy Matters
There are several reasons why privacy matters in the digital age where users and enterprises are increasingly storing data in the public cloud. It is estimated that more than a third of people’s data is in cloud storage today.
What may seem like disconnected pieces of information from discrete parts of this data, can be pieced together to know things about businesses and individuals that they didn’t intend to share in the first place.
Secondly, what you may consider ok to share today, may not be something you consider ok to share down the road – but once data is in the cloud, the lack of control makes it virtually impossible to go back and change your mind.
Last, but not least, privacy policies that you “accept” when signing up with cloud storage vendors can change and are virtually impossible to keep track of.
Why Data Privacy Matters Even More for Businesses
Most discussions around data privacy center around the rights of individuals. But with regulations like GDPR that have effectively shifted the accountability around privacy to businesses, the privacy of data has become a business / regulatory problem.
If one thinks about it a little, Data privacy can be a bigger problem for businesses than for individuals. Most individuals at some level, are willing to trade some privacy for convenience. Businesses have too much at stake to allow any breach in privacy of their data. The resulting penalties can be enormous.
Let’s take a look at this in the context of the cloud. An individual may be ‘ok’ having some private information made available to Google in return for flight reminders, weather updates, and traffic tips. So, uploading a boarding pass into Google docs may not seem like a big deal. But an enterprise may not be comfortable allowing flight information for a senior executive is accessible to anybody other than who needs to know.
Data Privacy Issues
When businesses use data management solutions like backup, data archiving, file collaboration, and file sharing solutions – the decision about where to house the data repository backing these applications becomes an important question.
While using services like Google Docs, OneDrive for Business or Dropbox may seem straightforward enough, SaaS services such as these which utilize public cloud infrastructure, pose a bevy of challenges for a business’ security team.
Most SaaS vendors today offer to encrypt the data sitting in their data centers, but the encryption comes with some risks.
- Most public cloud vendors own and control the encryption keys, or at the least retain the ability to decrypt data with keys the customer might actually control. This means that they are in a position to decrypt data at any time and gain access.
- Public cloud vendors don’t usually go out of their way to access their customers’ confidential data, but the chances of a cloud provider gaining unwarranted access to critical customer data are far too likely for the comfort of most enterprise security teams.
- Also, if asked by government bodies to turn over sensitive data, many public cloud vendors have no choice but to immediately comply and share data in decrypted form, because the laws of the land may require them to do so.
How Parablu Helps with Data Privacy
Parablu’s Private Storage Container, BluKrypt™ with its secure cloud gateway has been designed to protect enterprise data in the cloud. BluKrypt doesn’t merely encrypt data – it obfuscates it thoroughly. File names, folder names, etc. become undecipherable on the target storage when BluKrypt™ is in use. Files may also be chunked up into smaller components and encrypted separately. All data processed by BluKrypt is encrypted both in-flight and at rest. When in flight we use TLS 1.2 with strong ciphers.
Segregation of Duties
But more importantly, BluKrypt operates on an important principle in encryption called the Segregation of Duties (SoD). When done correctly, SoD is a risk and security measure that ensures no two parties can perform the same part of a critical process or function. By dividing responsibilities and limiting access to information and data on a strictly need-to-know basis, organizations can significantly reduce their risk. Many organizations already successfully implement SoD in other areas of their business, such as in their finance teams.

- In the physical world, as a society, we have surmounted this problem already, and use SoD where we must. The best analogy is safe deposit box in a bank. You may use the bank’s premises to keep valuable belongings – just like you may use the cloud to store valuable business data.
- But when you rent a safe deposit box, you also have the option to lock it and bring a key back with you – thus ensuring you exclusive access to your belongings.
BluKrypt ensures that piecing together data off the target cloud storage is completely impossible unless the user authenticated themselves appropriately, at which point, BluKrypt™ de-obfuscates and decrypts the data back to its original form.
BluKrypt helps enforce SoD for enterprises, by encrypting data before it ever leaves their trusted environment and ensures that they retain sole custody of the keys. Thus, by deploying the BluKrypt™ Gateway inside their network perimeter and routing all backup traffic through it, businesses can ensure that the backup data stream is encrypted on-premise before traveling to its cloud storage destination. This encryption is persistent in that it isn’t just encryption “in-flight” – the data remains encrypted with the business’ keys even once the data reaches the cloud destination and is at rest. Also, the business holds and retains complete control of the encryption keys.
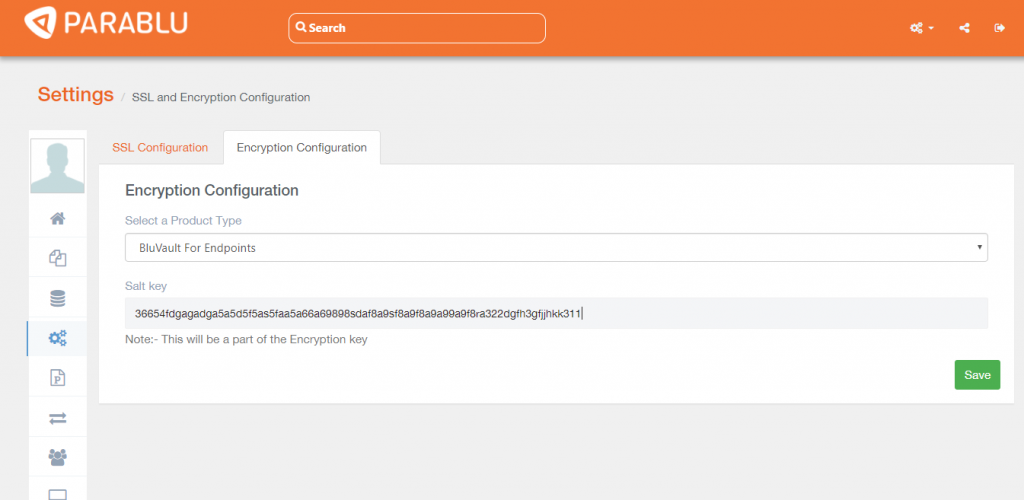
BluKrypt never actually stores actual keys anywhere on disk. Keys are always generated on-demand, utilized only in memory for an encryption/decryption operation, and then discarded. The IT administrator can, however, at any time effect a change for all their user keys simply by changing a parameter in the Parablu management interface, called an Initialization Vector (IV). The IV is an important ingredient that goes into the generation of the keys – and by having control of this element, businesses can change their encryption keys at any time.
Enforcing strict SoD is an important step towards satisfying current and future privacy regulations such as the GDPR. As a result of this combination of encryption + SoD, the BluKrypt container provides what we call “Zero Knowledge Privacy”.
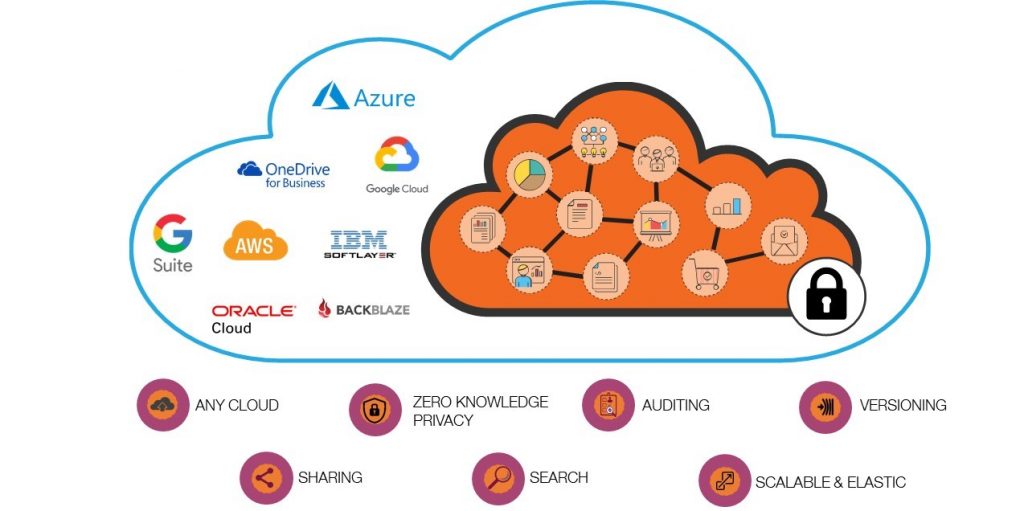
The Power of Parablu’s Private Storage Container
But the container is much more than that. All data in the container is not only encrypted, but all data is also versioned, searchable, shareable, and all accesses are audit-logged. It is storage agnostic and works with equal facility with any cloud storage target or even on-premise disk. It is a complete object storage platform that can be utilized for several data management applications – especially those requiring security and privacy.
If you are an enterprise or mid-sized business using the cloud, ask yourself if your business data is being kept sufficiently private. It is better to ask and have this question answered before it is too late.




