Unusual Activity Detection – Identifying and Flagging Security Threats

Ransomware attacks have become rampant and commonplace. As a data security measure, many enterprises worldwide have relied on cloud-based backups. However, just backing up data is insufficient to thwart data loss risks posed by evolving cyber threats. The biggest challenge is to detect an attack early.
Several organizations fail to detect anomalies early and realize they are ransomware victims only after finding their critical files either inaccessible, corrupted, or lost. Worse, enterprises are not equipped with a recovery mechanism to get back the lost data. A survey found that in 2022, 87% of victim enterprises paid a ransom in the hope of recovering their data.
Early detection is one of the surest ways to prevent such situations and mitigate ransomware as well as its associated risks and penalties.
What is Unusual Activity Detection?
Unusual activity detection looks to identify potential data security threats so that they can be investigated and mitigated before any harm is caused. Unusual patterns of network traffic, suspicious user behavior, and unexpected changes to system files are a few basic identifiers. Detection can be carried out by harnessing machine learning algorithms to analyze data from various sources and look for patterns or behaviors that deviate from the normal, or the usual.
While it appears utopic, Unusual Activity Detection is the most challenging phase of incident detection. With the aim to overcome this challenge, BluVault, Parablu’s flagship data resiliency solution, has significantly increased detection and remediation capabilities. This is a game changer in the industry and clearly enables enterprises to turn the tables on attackers.
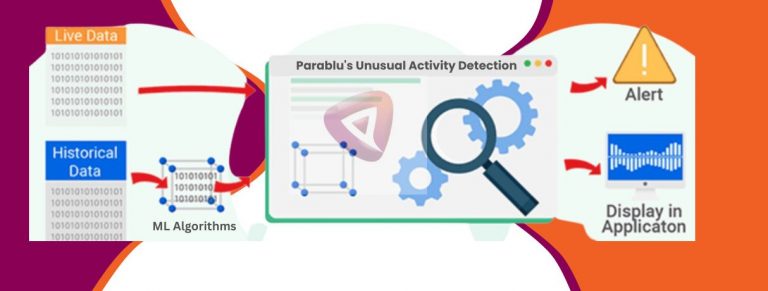
With the unusual activity detection ability ingrained in Parablu’s data security and resiliency solution, BluVault, detects and warns IT administrators about the possibility of ransomware attacks early. Further, it doubles up as a data recovery safety net that ensures no critical files are lost, allowing businesses to run uninterrupted.
- Data Parsing
Parablu employs machine-learning algorithms to scan enterprise data on a regular basis to detect ransomware-infected files. These algorithms also raise a flag if there are unauthorized modifications in a file’s content.
Identifying patterns of deleted files or encrypted files during incremental backups is a way of knowing if an enterprise is a victim of a ransomware attack. Along with Machine Learning, several other statistical models are used to compare files with historical data and compute a score that determines the likelihood of an enterprise being under attack.
- Unusual Activity Detection Dashboard
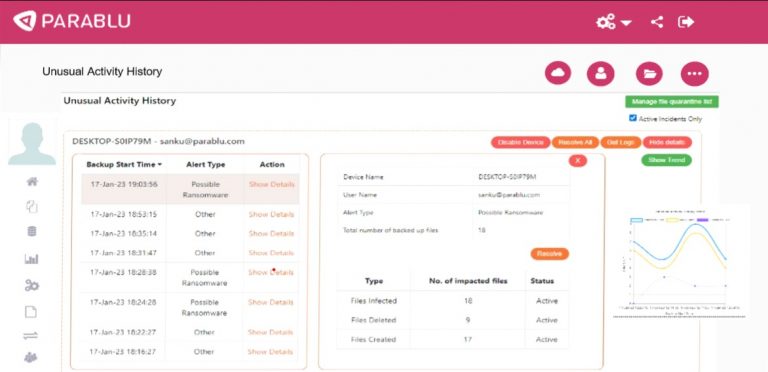
Parablu can remove the infected file altogether or even retain a copy, depending on the enterprise’s preference. In either case, the administrator is informed about the data corruption incident. The Unusual Activity Detection dashboard warns administrators of attack possibilities through a series of notifications. The portal also displays infected file history and their trends across devices over a period, offering IT administrators an unmatched degree of transparency.The image below reveals details displayed in the unusual activity detection dashboard.
Unusual Activity Detection is one significant element of the overall robust data resiliency solution from Parablu. Let’s delve deep into other benefits of Parablu’s data security solution. So what makes BluVault a comprehensive and highly recommended data resiliency solution, changing the game of the fight against ransomware attack?
Benefits of Parablu’s Data Security Solution
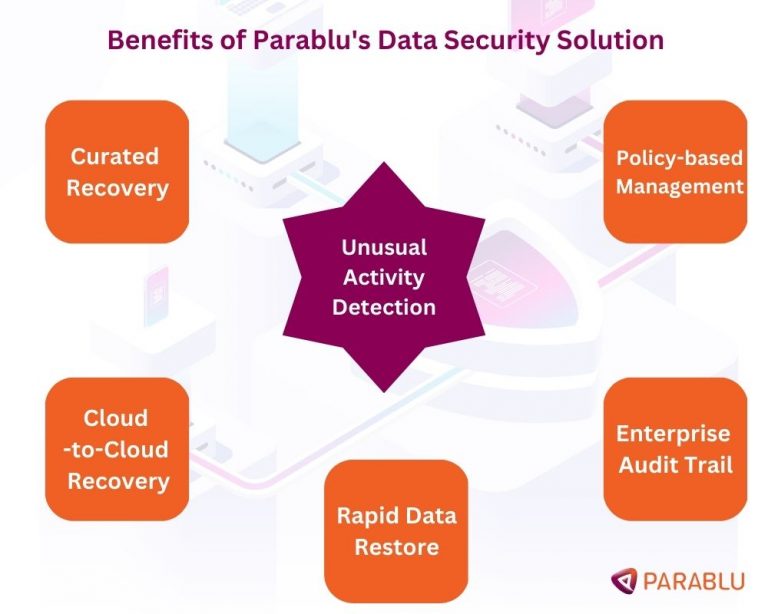
- Curated Recovery
Users can inform Parablu about roughly when the attack started to the current time. Parablu identifies the exact stolen files by utilizing its metadata catalog to bring back the previous good version of the file. The result is a dramatic reduction in the data recovery and business downtime.
- Policy-based Management
BluVault by Parablu has granular controls by way of policy-based management, enabling administrators to effortlessly manage backup behavior, including backup schedules, folders to include/exclude, file types, number of versions to keep, file size limits, user quota limits, etc. The required customization can be seamlessly performed using an intuitive, DIY dashboard.
- Enterprise Audit Trail
The BluVault system is fully auditable with all touchpoints monitored automatically. Managing backups is made simple with a user-friendly dashboard and detailed reports.
- Rapid Data Restore
A big differentiator is that BluVault can rapidly restore “dehydrated” versions of user data, which takes only a fraction of the time compared to restoring complete files. These dehydrated files function as clickable links or shortcuts to the original files, enabling users to access their data while the complete data restore runs in the background. As the fully restored files arrive from the backup repository, they automatically substitute the dehydrated copies.
- Cloud-to-Cloud Recovery
Parablu can restore data from cloud repositories directly into a user’s OneDrive account, ensuring data is restored faster. The approach prevents significant dependency on network bandwidth and helps do away with checks such as ensuring endpoints are always on and connected.
Unusual Activity Detection – Common Use Cases
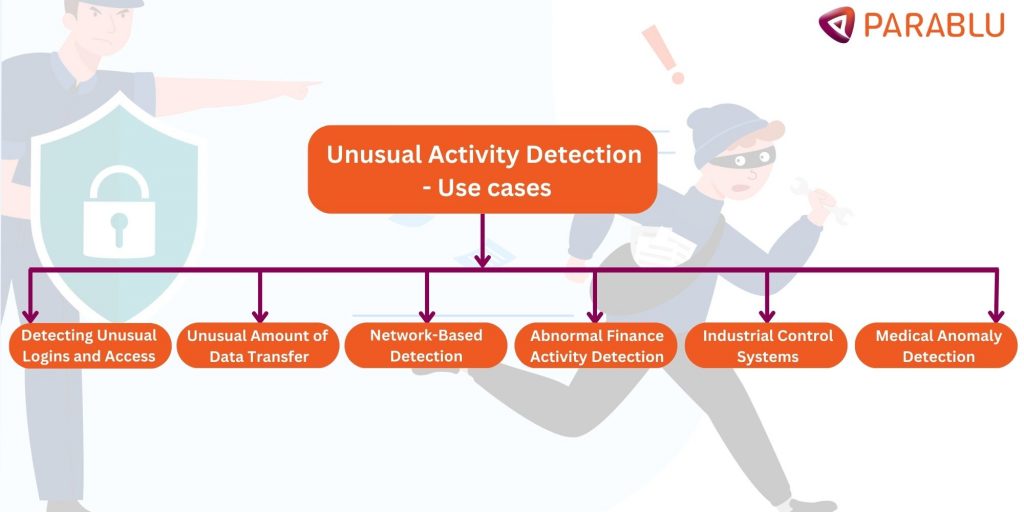
- Detecting unusual logins and access
Several employees travel for business purposes and access a company’s confidential intellectual property, such as competitive insights and pricing. Accessing such critical organizational information through various devices, including laptops, mobile phones, and even public systems, often exposes it to cyber-threat risks. This poses a huge challenge to the current security systems to distinguish
between authorized users and attackers, who may steal credentials through social engineering or targeted malware.
Analysing user behavior is necessary to identify attackers, as unusual activity can indicate that the individual accessing the assets is an unauthorized user. For instance, it may be possible to detect if an employee has accessed data that they have never used before or if they have logged in from a location that is geographically impossible to have travelled between attempts.
When such patterns are identified, swift action can be taken, such as immediately suspending user access rights.
- Unusual amounts of data transfer
An abnormal instance or pattern of large of data getting transferred between users is an event that is a big clue hinting at a possible anomaly. In addition, watching out for data being transferred to unusual locations or machines are red flags to watch out for.
- Network-based Detection
Recent years have witnessed an increase in the number of web-based businesses and virtual stores. Many of these online portals have been the victims of DoS (Denial-of-Service) attacks. Analyzing the network traffic of these portals can help minimize the impact of these attacks.
- Abnormal Finance Activities Detection
An organization’s financial transactions are usually confidential and entrusted only to a handful of individuals. Yet critical financial data is often compromised due to numerous reasons. In the recent past, several cybersecurity teams have adopted Machine Learning to compare historical and current data to detect financial fraud. However, currently, only behavior-based anomaly detection can be employed to prevent malicious financial activities and other threat investigation methods are being discovered.
- Industrial Control Systems
Sensors employed in industrial machinery often serve as anomaly vectors. The data patterns emerging from these hubs can also be analyzed to detect machinery malfunctions and prevent further damage.
- Medical anomaly detection
Clinical settings have utilized outlier identification in diverse ways. One application involves using density-based clustering to analyze patient care flow logs for anomalous traces. Medical image analysis benefits from detecting anomalies to improve diagnostic precision, and scrutinizing treatment plans can reveal life-threatening errors.
The Parablu Advantage
Parablu’s data security solution suite is a double delight for IT administrators since it warns them of cyber-attacks by raising flags and helps enterprises seamlessly recover lost data with very low latency. In addition, being equipped with Parablu’s enterprise-grade data security solution also helps organizations stay regulatorily compliant with patented secure cloud container options.
Sign up for a demo to learn more about Parablu’s data security and resiliency solution and its Unusual Activity Detection ability or simply write to info@parablu.com.




