Parablu’s Guide to 2024 Ransomware Playbook

Ransomware incident response is the need of the hour. Let me explain you why-
Ransomware attacks have evolved to become a critical threat in 2024, while recovery from such an attack increased drastically from $1.82 million in 2023 to a whopping $2.73 million this year—which is sans any ransom paid out. Healthcare organizations have fallen victim quite badly, where the cost of data breaches increased by 53.3% since 2020. Experts predicted that by 2031, a ransomware attack would strike every two seconds.
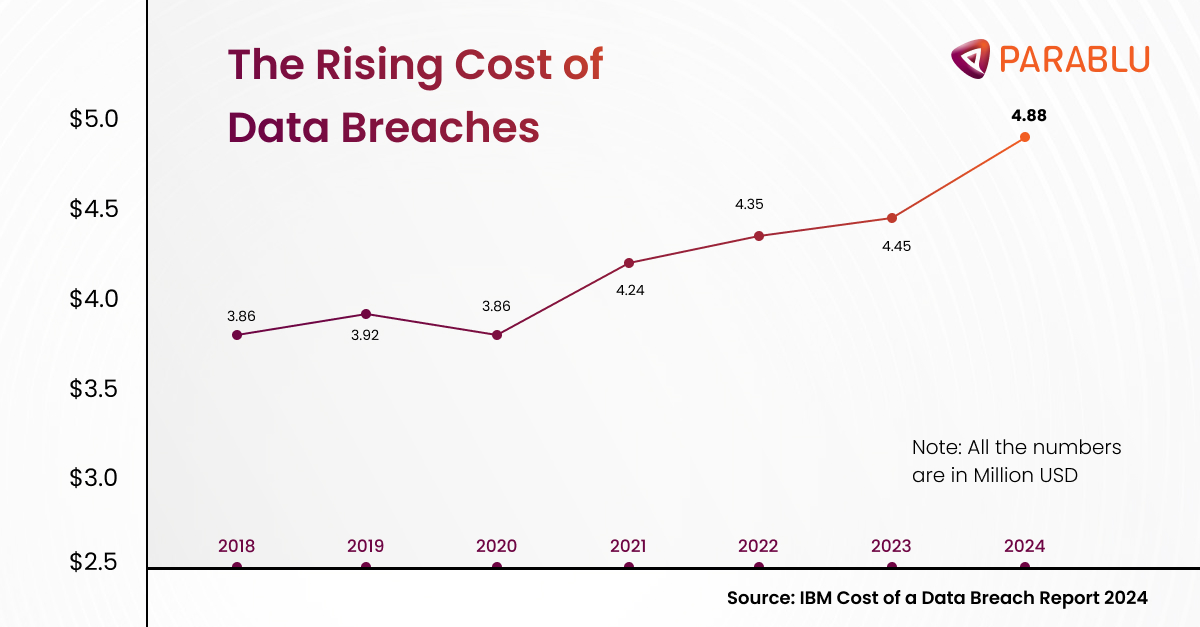
Recent events demonstrate just how far-reaching and destructive these attacks can be. Last July 2024, a phishing attack exposed sensitive personal data in a breach that hit the governing body of Formula 1, FIA. Weeks later, BMW Hong Kong announced the exposure of customers’ personal details, amounting to 14,000. As recently as 5 August, McLaren Health Care, one of Michigan’s biggest health systems, was under ransomware attack. IT systems across 13 hospitals were paralyzed, which placed patient records and payroll in jeopardy. These stand as warnings to businesses both small and large.
Having a comprehensive ransomware incident response now is no longer an added extra—it is a must. Here’s how businesses can fortify their defenses in 2024.
Understanding the Evolution of Ransomware Attacks
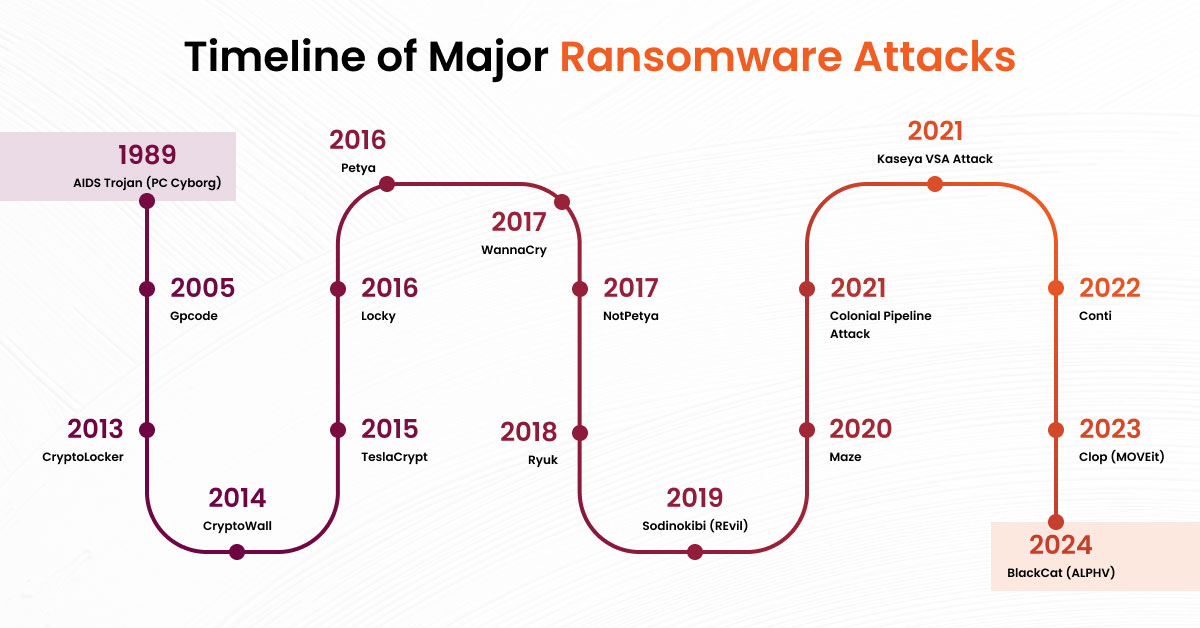
Ransomware did not start as the terrifying, convoluted monster that it is today. Things were simple: stuff your file folders with locks and call for a small sum to give them back. Annoying? Right. World-ending? Not really. But years passed, and ransomware got big and bloated into a real nasty threat.
These were more of a nuisance, happening during the early 2000s, producing headaches but doing little damage. Move on to the 2010s, when things started to change. Ransomware attacks got smarter and more dangerous, but have you revamped your ransomware incident response steps. Do you remember WannaCry in 2017? That was a big one. It crossed continents and thumped businesses, hospitals, and even governments while demanding instant money in cryptocurrency.
Today, ransomware is on a different level altogether. Hackers no longer attack just individuals; they attack entire companies, health systems, and even governments. The money they ask for is huge. It’s no longer only the tech-savvy criminals who can set up an attack; anybody can do so through ransomware-as-a-service. In other words, something that was a simple trick has become a global problem. To stay safe, all of us need to become much more aware and prepared for whatever is coming next with a planned ransomware incident response.
Why does your business need a ransomware incident response playbook in 2024?
Ransomware attacks are more frequent and destructive than ever in 2024. These attacks have turned from being an annoying hindrance to one of an existence-threat-level events that could put your business on its knees within minutes. The question is no longer “if” but “when” you will be a target in 2024. The ransomware playbook is, in essence, the incident response plan for your business—a concise ransomware incident response steps of playbook helping to safeguard your firm before, during, and after an attack.
Unless one has a plan in place, it could cause real chaos, lost data, and massive financial losses by halting operations. At a high level, the ransomware playbook can help to prevent this with several key steps laid out on prevention strategies, such as good encryption practices, constant employee training, and threat detection systems on par with the latest technological innovations, and response tactics like immediately isolating affected systems, secure channels of communication during an event, and ways of engaging with law enforcement.
Recovery plans that should be developed to restore data and system functionality with the least possible downtime.
The playbook takes that panic and turns it into action. If you suffer an attack, your team won’t be rushing. They will be aware of how the isolation of infected systems, warning of key people, and enabling of fast start of the recovery process are done to reduce downtime and cost. You leave your business in a very vulnerable state without a playbook. However, by implementing ransomware incident response, you will be prepared, confident, and in control.
Secure Your Business Now – Get a Ransomware Protection Plan!
An effective ransomware incident response playbook is very much like a carefully thought-out battle plan for defense against cyber threats. In fact, it all starts with preparation—that is, laying the foundation of your defense—by which you will have your policies in order, roles defined, and tools available at your command prior to any event. This assures you that your team can act fast when called upon to do so.
Next in line is identification, where you detect and confirm the occurrence of a security incident. It’s kind of an early warning system that warns you that something is going on. Right after identification is the very important phase of containment. What that does is isolate the threat, limiting its propagative power, hence further potential damage.
Moving on to eradication, where malware or other malicious elements are now totally removed from your systems. Recovery follows threats have been eliminated; this is for system restoration to normalcy and assurance of business continuity.
Finally, lessons learned, where you will analyze the incident, find out how you can do it differently next time, and enhance the playbook to become more effective during future incidents.
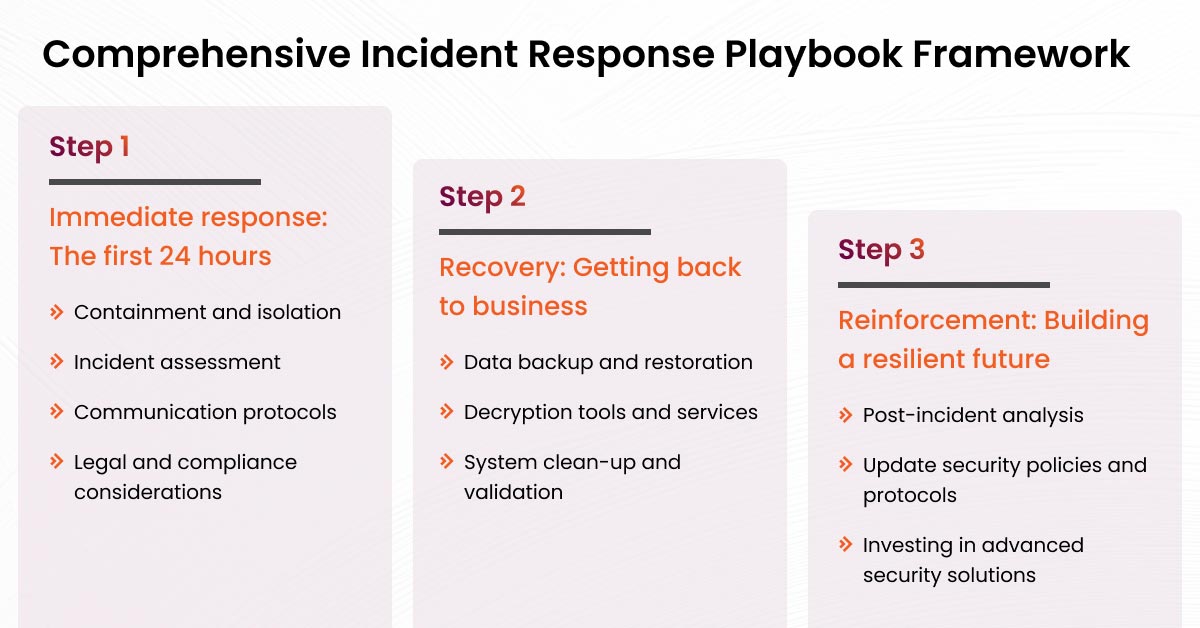
Step 1: Immediate response: The first 24 hours
The first 24 hours are rather critical in terms of the swiftness of action for mitigating ransomware damage. This will focus on containing the effort and protecting your organization from further threat actors.
Containment and isolation
First, affected systems must be isolated to prevent the spread of ransomware. That would partially be successful by disconnecting from the internet, switching off wireless functionalities, and segregating compromised devices from the network.
Incident assessment
First, the situation is assessed in terms of its scope and potential impact. It involves knowing the ransomware variant, which systems are compromised, and what data could be at risk.
Communication protocols
Communication plays an important role in cybersecurity incidents. Communication protocols provide a straightforward path for information on status and response actions to the IT staff, management, or external partners or stakeholders.
Legal and compliance considerations
It cannot let its guard down over legal and compliance obligations in the case of a ransomware incident. Enterprises need to be aware of and fulfill all laws and regulations that apply, possibly seeking legal counsel to navigate these complexities and ensure adherence to legal obligations.
Step 2: Recovery: Getting back to business
Given the demands placed upon businesses today, rapid recovery is required. Robust backup solutions make sure that you will experience minimal downtime, save all your critical data, and get running again without missing a beat.
Data backup and restoration
Regularly back up important data to secured, isolated storage, such as the cloud. In an incident of ransomware, ensure that the backups are clean and untouched before applying them to get back to work and eliminate reinfection possibilities.
Decryption tools and services
In case of ransomware attacks, look for the tools available or professional services that can unlock files without the need to pay the ransom. Experts do it, but it is expensive. It isn’t always guaranteed to work, so consulting the experts in cybersecurity is very important.
System clean-up and validation
Thoroughly clean your systems to remove all traces of ransomware before fully restoring operations. Use advanced antivirus and malware tools, and perform rigorous checks to ensure no remnants remain, safeguarding against future attacks during the recovery process.
Step 3: Reinforcement: Building a resilient future
The reinforcement strategies will thus help in building a resilient future with stability and adaptability against challenges. Strategic and proactive measures at an organizational level will protect the data against disruptions.
Post-incident analysis
After a ransomware attack, a post-incident analysis is important to understand how the breach took place and for learning purposes. This should include the entry points, the extent of damage, and response effectiveness. The review is supposed to bring out such insights, which will then direct how to strengthen systems and processes to prevent future attacks.
Update security policies and protocols
Businesses should change security policies and protocols in line with the discoveries that result from a post-incident analysis. This might involve enhancing the access control policies, tightening the e-mail security policies, or setting up more rigorous network monitoring practices. It is very important that these policies get changed as often as necessary and are kept current in respect of new threats that might manifest and put business data at risk.
Investing in advanced security solutions
Advanced ransomware incident response fortifies defenses against future ransomware attacks. Such solutions may include endpoint detection and response systems, sophisticated antivirus programs, or AI-driven threat detection tools. Businesses that regularly invest in and update these technologies will be far ahead of cybercriminals, ensuring no major disruption from ransomware or other cyberattacks occurs.
How often should I refresh a ransomware incident response playbook?
The business environment is constantly evolving, driven by new technologies, market trends, and emerging challenges. If your playbook remains unchanged, it risks becoming obsolete, leading to inefficiencies or even strategic misalignments. Regular refreshments help ensure that your strategies are up to date, align with your current business objectives, and equip your team with the latest tools and insights.
A good rule of thumb is to review and update your ransomware playbook every 6 to 12 months. This period is long enough to gain worthwhile perspectives from recent experience but short enough that you will be able to respond to important changes in your industry. That said, such frequency may vary independently of the pace of change in your business environment. In fast-moving industries, updates may need to be more frequent.
Watch Webinar ▶️ Recovering from Ransomware: Cracking the Code with Top Experts
What to consider during a ransomware incident response playbook refresh?
When refreshing your ransomware playbook, consider the following key areas:
- Market and industry trends: Has there been a relevant change in your industry that requires adjustments in your strategy?
- Technological developments: Have any new tools or technologies been developed that will improve your processes or give you a competitive edge?
- Team feedback: What have your team members learned or experienced that the playbook should cover?
- Performance metrics: Check key performance indicators to see if the strategies in use are still yielding the desired output.
- Make it a habit to revisit and update your ransomware playbook every 6 to 12 months, and you’ll find that this small investment of time pays off significantly in the long run.
Conclusion
In such a volatile landscape of modern cyber threats—notably, ransomware attacks—a proactive approach, coupled with a strong incident response playbook, will go a long way in fortifying an organization’s cybersecurity posture. By designing the strategies, a business can considerably reduce the effect of ransomware and be much better prepared against such pervasive threats. The idea is to defend, prepare, and ensure continuity and security in the digital age. By taking these steps seriously today, you shall be arming your business against ransomware attacks—to 2024 and beyond.




