Encryption Key Management – What You Need to Know

Encryption key management is a significantly important data protection aspect to be understood and practiced to ensure critical files are indecipherable to attackers. Conventional file-sharing protocols encrypt data only in transit but not at rest and offer no control over the receiver’s actions. Mere password-protected files and cloud backups must make way for better data protection measures. Although recommended encryption practices have been implemented by several enterprises already, they must revisit and improve to circumvent rising threats.
What is an Encryption Key?
Encryption key simply means a cryptographic combination of bits, like a password, that is used to cipher data into a form that is not readily decipherable or usable without authorization. The longer the keys are, the harder it is for unintended entities to recreate. While 128 and 256 bits are the recommended lengths for private keys, 2048 is the preferred public key length. Later in this document, we deep dive into the types of encryption keys.
How Encryption Keys Determine Data Safety
Cloud vendors are trusted with data security and scalability. However, subscribers of these storage models are assured of their data’s safety but not necessarily exclusive data privacy.
Check : How Data Encryption Works?
Picture this: You are assured of the safety of your belongings in a bank’s vault. However, not owning and not having sole access to an exclusive key to the locker should raise obvious privacy concerns. Similarly, cloud vendors offer you data security but not absolute data privacy.
Parablu’s Solution Suite
Built on a patented data protection technology, Parablu’s solution suite, comprising of BluVault and BluSync™, offers you data security, resiliency, and zero-knowledge privacy.
Here are a few benefits of Parablu’s solutions.
- Zero Knowledge Privacy
Parablu’s solution is built on the fundamental principle of Zero-Knowledge Privacy and grants enterprises complete authority over their encryption keys. The approach can simply be summarized as Bring Your Own Key (BYOK). The BYOK approach doesn’t just make you ransomware ready but also gets you to be regulatorily compliant – this is a must-have recommended encryption best practice. This means only organizations have access to their data, no cloud vendor, not even Parablu’s team.
- Data Obfuscation
Parablu’s patented data protection technology leverages obfuscation, an approach that is a level above encryption. Files and folders are decomposed into small, separately encrypted portions, creating a digital jigsaw that is highly resistant to threat actors. While encrypted files can be made readable if the authorized user somehow possesses the right key, data that is obfuscated using the data-shredding technique described above can be decrypted only by authenticating as an authorized user and letting the software perform the decryption and re-sequencing of the data shreds.
- Regulatory Compliance
Parablu’s encryption practices are aligned with regulatory standards such as Sarbanes-Oxley Act (SOX), Health Insurance Portability and Accountability Act (HIPAA), and General Data Protection Regulation (GDPR), helping enterprises stay compliant.
- Cloud-Agnostic Zero Storage Costs
Parablu’s solution suite can be seamlessly integrated with multiple cloud storage models such as Amazon S3, Google Cloud, and Microsoft Azure. Parablu’s solution suite can be easily integrated with OneDrive for Business and Google Drive accounts and does not incur any additional storage costs. This implies huge savings on the Total Cost of Ownership (TCO).
Parablu’s BluVault-Powered Encryption
BluVault is an enterprise-class data backup solution that leverages a secure container technology that encompasses best-in-class encryption practices. It encrypts data both at rest and during transit – a recommended practice, and helps enterprises stay regulatorily compliant. The product effectively overcomes several data protection challenges. BluVault offers you both security and zero-knowledge privacy. To draw a parallel with the banking example, this simply means you own the keys to your vault.
- Protection Against Full-Disk Encryption Mishaps
BluVault’s backups are ideal for endpoints with full-disk encryption software installed. Corruption of the software could deem the entire endpoint data inaccessible and a modern data backup solution such as BluVault could prevent such a mishap.
- Enterprise Audit Trail
BluVault delivers detailed, granular reports of the various data backup activities that are easily auditable.
- Quick Data Restores
BluVault enables administrators and users to initiate automated restores through an easy-to-use interface effortlessly.
- Segregation of Duties
Segregation of Duties (SoD) is an exclusive BluVault feature in that no two individuals are involved in the same activity. From an encryption key generation perspective, the practice ensures exclusivity and prevents one party from tampering with the activity of the other.
- Encryption Key Management
Parablu’s secure container technology offers enterprises the authority to define their encryption keys, which are neither stored by the cloud vendor, nor even Parablu. The solution allows enterprise customers control over the encryption keys via an ingenious ‘salting’ mechanism that lets enterprises retain control over keys without expensive and onerous key management software. Using this built-in Segregation of Duties, BluVault uses industrial-strength AES-256 encryption to preserve data at rest. BluVault also has the option to integrate with cloud HSMs like Azure KeyVault if customers so desire. In either case, the practice ensures a strict Segregation of Duties leaving no room for exposure or compromise.
BluVault encrypts data both at rest and during transit – a recommended practice, and helps enterprises stay regulatorily compliant.
Don't Miss Out—Subscribe for Exclusive Updates!
Protect your critical data with our reliable backup solutions.
BluSync™ – Enterprise File Sync and Sharing
Conventional file-sharing methods such as the Secure File Transfer Protocol (SFTP) encrypt data only in transit. However, BluSync-powered Managed File Transfer encrypts data both in rest and transit and offers several more benefits.
- Secure File Transfer
Public cloud transfer services, the preferred file-sharing approach, offer no encryption control to the users. BluSync™ encrypts data both at rest and in transit, enables users to define complex passwords, as well as helps implement Multi-Factor Authentication (MFA) and Integrated Rights Management (IRM) controls.
While MFA serves as an additional authentication measure to a password, IRM prohibits users from performing actions such as downloading, saving, and printing.
BluSync™ encrypts data by adopting Multi-Factor Authentication (MFA) and Integrated Rights Management (IRM) controls.
- Secure Share
BluSync™ enables sharing data using password-protected, self-destructing URLs, and is equipped with built-in anti-malware scanning ability. The product also allows users to easily un-share a file in case of an error, or as soon as a security compromise is suspected.
- Full-Text Search
BluSync enables users to retrieve content within files or folders by specifying keywords or phrases.
Types of Encryption Keys
Here are a few details of the types of encryption keys. In the following sections we will learn about Encryption Key Lifecycle Management and some encryption best practices.
- Symmetric Keys: Data-at-Rest
A single key is used by conventional file transfer protocols to encrypt data stored in a database. The required documents can be deciphered by a set of authorized users only. The keys to encrypt and decrypt are identical.
- Asymmetric Keys: Data-in-Motion
Protecting data in transit is an advanced cybersecurity approach, where a pair of keys, namely private and public keys are utilized to create ciphertext and decrypt when required. The public key encrypts the data but cannot be used by the receiver to decrypt, whereas the private key can only be used to decipher the text.
The example of session keys used in a Virtual Private Network (VPN) to encrypt and decrypt the data shared between a sender and receiver best illustrates the functioning of both these keys.
The longer the keys are, the harder it is for unintended entities to recreate. While 128 and 256 bits are the
recommended lengths for private keys, 2048 is the preferred public key length.
Encryption Key Lifecycle Management

Generation
The primary step is to ensure the key generated is secure enough to prevent data exposure. Keys generated by adopting weak encryption algorithms and/or storing in unsecured locations could make them susceptible to cyber threats. Leveraging AES (Advanced Encryption Standard) algorithms help generate keys that make data hard to decipher for unauthorized actors.
Distribution
The generated keys are to be distributed among the file sharers and the adoption of the Hardware Security Module (HSM) is the most secure method. Utilizing a TLS (Transport Layer Security) or Secure Sockets Layer (SSL) connection is also a secure key distribution approach. HSMs are specialized devices used for performing cryptographic operations such as encryption, decryption, authentication, key management, and key exchange. Availing a cloud service provider’s assistance is a conventional key management alternative to HSM, but this also implies entrusting the vendor completely with your data. Owning the creation of your keys is recommended.
Rotation and Destruction
Rotation simply means the replacement of a key once its defined period expires. It can also be replaced or permanently destroyed from a key management database in case of suspicion of its exposure to threats.
Revocation
Revocation is the practice of making a key unusable for both encryption and decryption purposes despite its crypto period being valid. For example, it is a requirement that keys be revoked and recreated when an employee who is aware of the keys leaves your organization.
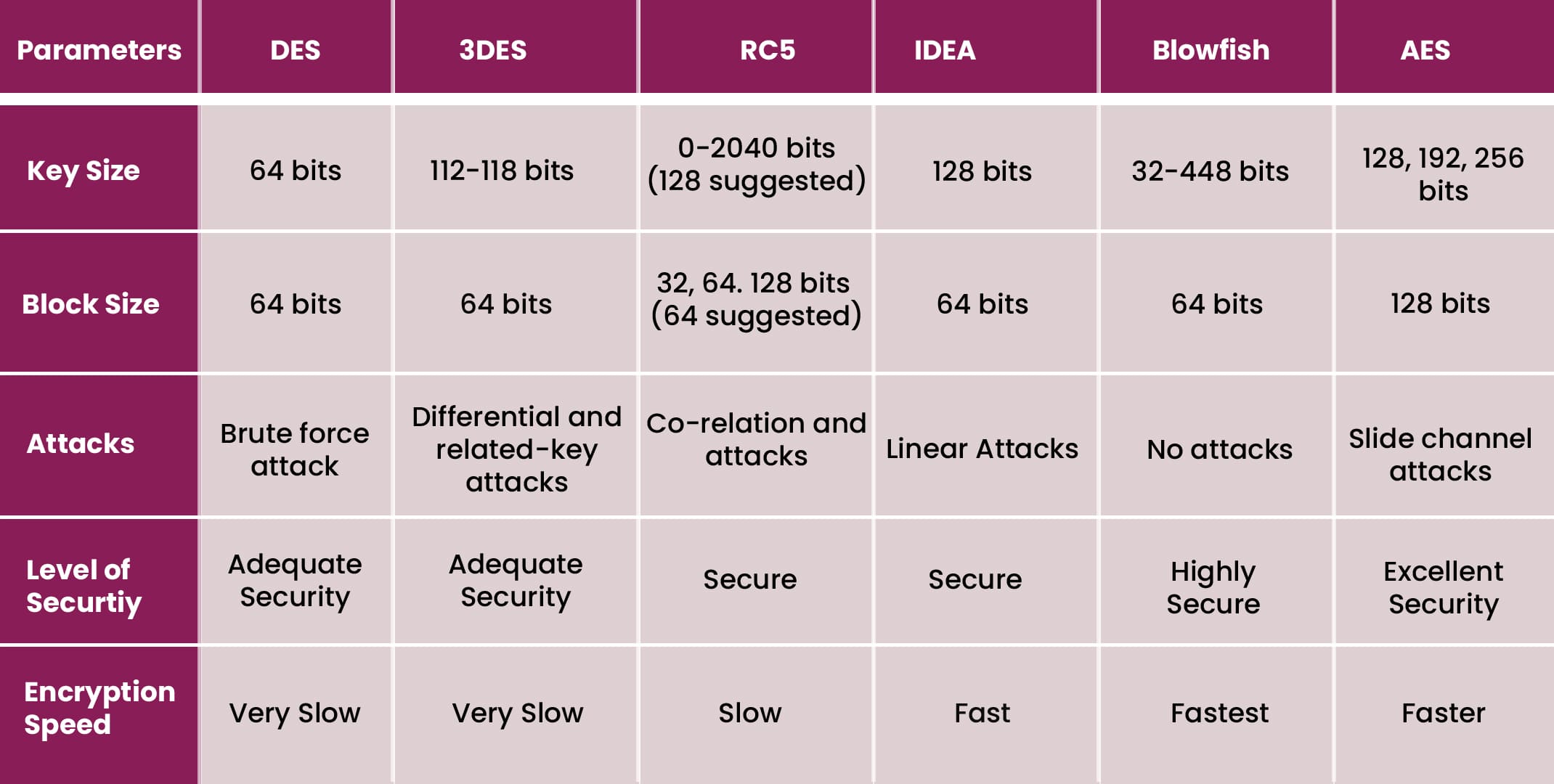
Image courtesy: https://www.researchgate.net/figure/Comparison-of-Symmetric-Cryptography-Algorithms-20_tbl1_328653330
Compliance and Best Practices in Encryption Key Management
Key management practices must adhere to regulatory standards such as Payment Card Industry Data Security Standard (PCI DSS), General Data Protection Regulation (GDPR), Federal Information Processing Standard (FIPS), and Health Insurance Portability and Accountability Act (HIPAA). Here are a few best practices recommended by cybersecurity experts.
1. Best Encryption Algorithms
A good combination of encryption algorithms and keys makes the data indecipherable to hackers.
- Triple Data Encryption Standard (DES)
The Triple DES is a much-improvised algorithm version of its predecessor, DES, which turned obsolete due to its high attack vulnerability. The total key length of the Triple DES is 168 bits, which includes three individual keys of 56 bits each.
- Advanced Encryption Standard (AES)
Considered relatively more advanced than the Triple DES, the AES is a standard utilized by the U.S government and is known for its highly efficient 128, 192, and 256-bit cipher combinations.
- RSA Security
Since RSA Security uses a pair of keys, it is considered an asymmetric algorithm that is difficult for hackers to crack since it demands significant time and processing abilities.
- Blowfish
Blowfish is freely available in the public domain and is considered one of the most effective symmetric key algorithms. Messages are divided into 64-bit segments each and separately encrypted in this cipher approach.
- Twofish
Another symmetric key algorithm, Twofish is tailored for hardware and software environments, and employs keys of 256-bit length each.
2. Least Privilege
Also known as the Principle of Least Authority (POLA), this approach believes in granting authorized users only a required set of privileges. For instance, allowing the user responsible for retrieving records from a database just the permissions needed to perform the job function and denying admin rights would prevent insider-caused breaches.
3. Hardware Security Module (HSM)
Since HSMs are devices that either must be stolen or physically accessed, they are less susceptible to attacks. Although cloud based HSMs are considered reliable key management options, a lapse in the cloud service provider’s security could enable the attacker to access the keys.
4. Segregation of Duties
The various key management duties can be segregated to prevent insider threats. For instance, allotment of the key creation, distribution, and access right management responsibilities exclusively to different individuals (or entities) would ensure no tamper. The entity generating the key would be nowhere involved in the distribution phase and so on.
5. Automation
All key management activities ranging from generation and distribution to destruction can be automated. Automation also ensures the key becomes invalid post-crypto period expiry.
6. Split Keys
The split key approach ensures two or more individuals are required to access a key. Since every person only has access to a part of the key, the security-compromised link can be easily identified.
7. Bring Your Own Key (BYOK)
Conventionally, cloud service providers own the encryption keys of their client data. Trusting a third-party vendor completely with the safety of encryption keys is an unsettling thought for most information security teams. The Bring Your Own Key (BYOK) practice, also known as Customer Supplied Encryption Keys (CSEK) grants enterprises complete ownership of the encryption keys used to secure cloud data.
8. Audit Log Encryption
A certificate can be used to encrypt audit logs and save them to a Keystore in an audit.xml format. The encrypted audit logs can be accessed only by a set of authorized users with passwords.
9. Periodic Key Rotation
Encryption key rotation is a practice followed to replace keys periodically to ensure less breach possibility. When an encryption key is changed daily and if at all a breach occurs, the hacker would be able to access only the data of the day.
Key Management Challenges
There are several key management challenges in businesses today which must be addressed.
- The encryption keys are usually controlled by the cloud service provider, giving consumers little authority over their data.
- Multiple user data are usually protected by the same encryption key by cloud vendors offering no distinction.
Key Management System
The encryption challenges posed by many keys generated because of growing data volumes can be mitigated by the adoption of a centralized Key Management System or KMS. An efficient KMS offers policy-based key generation, storage, and distribution. It also ensures the keys are securely archived and an enterprise audit log trail is maintained. The inclusion of KMS in an enterprise’s data protection strategy is an idea IT decision-makers should consider for securing encryption keys.
A vital factor that differentiates Parablu’s patented data protection technology from similar market variants is its Bring Your Own Key (BYOK) or Bring Your Own Encryption (BYOE) approach. BluSync overcomes dependency, or rather, the trust in the public cloud or SaaS vendor for data encryption needs. Conventionally, SaaS vendors could access customer data without permission at any time, but Parablu’s BluSync offers users complete autonomy over their encryption keys.
Ask for a free demo to learn more about Parablu’s encryption and data protection approach.



